O`Reilly – Kubernetes Security Attacking and Defending Kubernetes-iLLiTERATE
English | Tutorial | Size: 809.68 MB
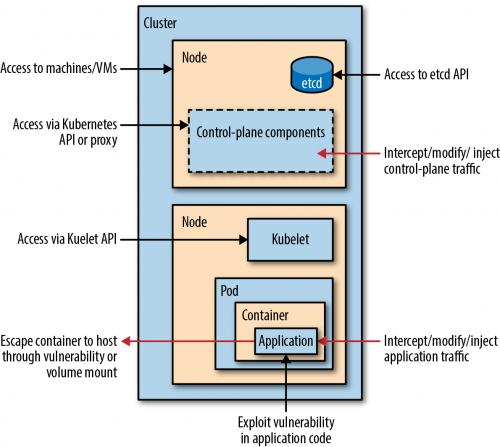
Like many complex systems Kubernetes has historically been insecure by default, [Read more…]
Get Yourself a Better Life! Free eLearning Download

O`Reilly – Kubernetes Security Attacking and Defending Kubernetes-iLLiTERATE
English | Tutorial | Size: 809.68 MB

Kubernetes Security – Attacking and Defending Kubernetes
English | Tutorial | Size: 809.31 MB

PentesterAcademy – (CRTP BootCamp) Attacking and Defending Active Directory: Beginner’s Edition
English | Size: 4.82 GB
Category: Tutorial
What You’ll Learn
This is a live session bootcamp with 4 chapters videos for beginner-friendly bootcamp, designed to teach security professionals how to identify and analyze threats in a modern Active Directory environment. [Read more…]

Infosec – Attacking Web Application Access Controls
English | Size: 332.12 MB
Category: Tutorial
Learn to attack web application access controls with this course on attacking access control, attacking authentication, attacking session management and more. [Read more…]

Gordon Ryan – Systematically Attacking the Guard
English | Size: 4.98 GB
Category: Health-Fitness

Pentester Academy – Attacking and Defending Active Directory (Complete Course)
English | Size: 4.73 GB
Category: Tutorial

Pentester Academy – Attacking and Defending Active DirectBookmark
English | Size: 3.94 GB
Category: Tutorial

Attacking Network Protocols: A Hacker’s Guide to Capture, Analysis, and Exploitation 1st Editi
English | Size: 28.54 MB
Category: e-Books
You’ll start with a rundown of networking basics and protocol traffic capture before moving on to static and dynamic protocol analysis, common protocol structures, cryptography, and protocol security. Then you’ll turn your focus to finding and exploiting vulnerabilities, with an overview of common bug classes, fuzzing, debugging, and exhaustion attacks. [Read more…]